Active Directory Oid 11g Synchronization Log
- Active Directory Oid 11g Synchronization Login
- Active Directory Oid 11g Synchronization Log In Firefox
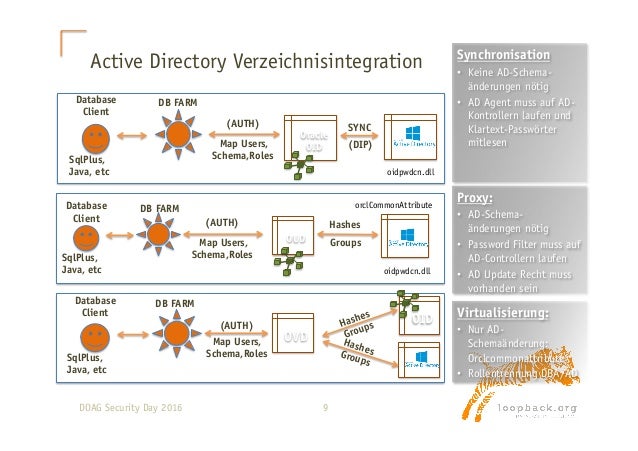
See Also:in Oracle Fusion Middleware User's Guide for Oracle Identity Manager for more information about LDAP synchronizationWhen Oracle identity Manager with Oracle Internet Directory (OID) or iplanet (ODSEE) or Active Directory (AD) is selected during installation, the virtualization functionality of Oracle Virtual Directory (OVD) is utilized. Oracle Identity Manager includes the Identity Virtualization Library (libOVD) instead of the stand-alone OVD server. Oracle Identity Manager deployment can be with or without Identity Virtualization Library (libOVD). With Identity Virtualization Library (libOVD) included in Oracle Identity Manager, the common library is used by Oracle Identity Manager without running its own instance of OVD.
Without Identity Virtualization Library (libOVD), Oracle Identity Manager must use an instance of OVD separately.When you select LDAP synchronization in the Oracle Identity Manager installer, you can select any one of the AD, iPlanet (ODSEE), OID, and OVD options. If you select any of AD, iPlanet (ODSEE), or OID, then Oracle Identity Manager is installed with Identity Virtualization Library (libOVD). If you select OVD, then LDAP synchronization is enabled, and no manual configuration steps for enabling LDAP synchronization is required. However, postinstall manual configuration to enable LDAP synchronization is required when LDAP synchronization has not been enabled at the time of installing Oracle Identity Manager.This chapter describes the following configurations for postinstallation enablement of LDAP synchronization:.In addition, this chapter contains the following sections:.
Note:In Oracle Identity Manager 11 g Release 1 (11.1.1), the idmConfigTool must be run to preconfigure LDAP synchronization. Running the LDAPConfigPreSetup script to preconfigure LDAP synchronization generates errors. See in the Oracle Fusion Middleware Installation Guide for Oracle Identity Management for information about using the idmConfigTool.Set the OIMHOME environment variable to the directory on which Oracle Identity Manager is deployed.Copy the following files from the MDS to a temporary staging directory, such as /tmp.
Note:It is mandatory to create a separate staging directory. The $OIMORACLEHOME/server/metadata directory cannot be used as the staging directory because it contains some other files. Note:The LdapContainerRules.xml file can contain rules by using only those attributes that are mapped to the directory. A rule cannot be written by using attributes from foreign objects or attributes that are not part of the entity. This is true for both user and role entities.
For example, Role Email cannot be used for rules for roles, and user's Organization Name cannot be used for user entity.Edit the LDAPContainerRules.xml. To do so, open LDAPContainerRules.xml, and replace $DefaultUserContainer$ and $DefaultRoleContainer$ with appropriate user and role container values. For example, replace:.$DefaultUserContainer$ with a value, such as cn=ADRUsers,cn=Users,dc=us,dc=oracle,dc=com.$DefaultRoleContainer$ with a value, such as cn=ADRGroups,cn=Groups,dc=us,dc=oracle,dc=com.Perform the import.
To do so:.Using the MDS utilities, such as weblogicImportMetadata.sh, available in the OIMHOME/bin/ directory, import all the files listed in step 2. Note:.See in the Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager for information about the MDS utilities.Make sure that EventHandlers.xml is in the /db/ldapMetadata/ directory when imported into MDS.MDS import utility imports everything in the staging directory, and therefore, only the files that are to be imported must be kept there. Otherwise, the Oracle Identity Manager instance can get corrupted.Navigate to the OIMHOME/bin/ directory.In a text editor, open the weblogic.properties file.
Provide values for the following properties:.wlsservername= oimserver1wlsservername is the name of the Oracle WebLogic Server on which Oracle Identity Manager is deployed.applicationname= oimIf you are importing or exporting any default event handlers, the value is oim. For rest of the predefined metadata, value is OIMMetadata. If you are importing or exporting any custom data, then use application name as OIMMetadata.metadatafromloc=/tmpThis is the directory location from which XML file is to be imported. For example, if you want to import User.xml and it is in the location /scratc/ USER/temp/oim/file/User.xml, then you can specify location value as /scratc/ USER/temp/oim.

Make sure that no other files exist in this directory or in its subdirectories. Import utility tries to recursively import all the files from location directory. This property is only used by weblogicImportMetadata.sh. Note:Similarly, to export the files, such as EventHandlers.xml, the path /db/ldapMetadata/EventHandlers.xml must be used. The value of metadatafiles in weblogic.properties must be:metadatafiles=/db/ldapMetadata/EventHandlers.xmlOIMHOME/metadata contains two directories, db and ldapReconJobs. The metadatafromloc location pointing to this directory results in import of both the directories into MDS.Run the following command to import the configuration files into MDS:sh./weblogicImportMetadata.shYou are prompted for WebLogic login information. Provide the following information: Please enter your username weblogic:weblogicPlease enter your password weblogic: PASSWORDPlease enter your server URL t3://localhost:7001:t3://localhost:8003This imports the configuration files.Edit IT Resource configuration in Oracle Identity Manager.
To do so:.Login to the Oracle Identity Manager Administrative and User Console by using administrator credentials, and navigate to Advanced Administration.In the Welcome page of the Advanced Administration, under Configuration, click Manage IT Resource. Note:The Oracle Identity Manager proxy user DN is in the following format:PROXYUSER,cn=system, ROOTSUFFIXFor example: cn=oimadmin,cn=system, dc=us,dc=oracle,dc=com.Make sure that the value for the Reservation Container is cn=reserve, VALUEOFTHEROOTSUFFIX. For example:Reservation Container: cn=reserve,dc=us,dc=oracle,dc=com.For reconciliation jobs, seed the LDAP Reconciliation jobs or Load LDAP Recon jobs into Quartz tables, which are part of Oracle Identity Manager schema. To do so:.Seed the LDAP Recon jobs by using the patchweblogic.sh MDS utility available in OIMHOME/bin/. 10.2.1 Enabling SSL Between Identity Virtualization Library (libOVD) and Microsoft Active DirectoryTo export the server side certificates from Active Directory and import into Identity Virtualization Library (libOVD):.Export the certificate from the Active Directory server by referring to the instructions in the following Microsoft TechNet Website URLs:.Retrieve the CA signing certificate and save it to a file. To do so:.Login to the Active Directory domain server as a domain administrator.Click Start, Control Panel, Administrative Tools, Certificate Authority to open the CA Microsoft Management Console (MMC).Right-click the CA computer, and select CA Properties.From the General menu, select View Certificate.Select the Details view, and click Copy to File on the lower-right corner of the window.Use the Certificate Export wizard to save the CA certificate in a file by running the following command: certutil -ca.cert OutCACertFile. 10.3 Provisioning Users and Roles Created Before Enabling LDAP Synchronization to LDAPIf you create users and roles in Oracle Identity Manager deployment without LDAP synchronization, and later decide to enable LDAP synchronization, then the users and roles created before LDAP synchronization enablement must be synced with LDAP after enablement.
The provisioning of users, roles, role memberships, and role hierarchy to LDAP is achieved by the following predefined scheduled jobs for LDAP:.LDAPSync Post Enable Provision Users to LDAP.LDAPSync Post Enable Provision Roles to LDAP.LDAPSync Post Enable Provision Role Memberships to LDAP.LDAPSync Post Enable Provision Role Hierarchy to LDAPFor details about these scheduled jobs, see. 10.4 Disabling LDAP SynchronizationTo disable LDAP synchronization in Oracle Identity Manager deployment:.Remove the /db/ldapMetadata/EventHandlers.xml file from MDS by using MDS utilities. To delete the XML file, modify the following values in the weblogic.properties file and run the weblogicDeleteMetadata.sh or weblogicDeleteMetadata.bat script:.wlsservername= OIMSERVERNAME, for example oimserver1.applicationname=oimIf you are importing or exporting any predefined event handlers, then value is oim. For the rest of the default metadata, value is OIMMetadata. If you are importing or exporting any custom data, then always use application.metadatafiles=/metadata/user/custom/EventHandlers.xml.Login to Oracle Identity Manager Administrative and User Console with administrator credentials.Disable all scheduled jobs mentioned in. 10.5 Managing Identity Virtualization Library (libOVD) AdaptersIn an Oracle Identity Manager deployment with LDAP synchronization enabled and AD, iPlanet (ODSEE), or OID as a the directory server, you can manage the Identity Virtualization Library (libOVD) adapters by using the WLST command.To manage the Identity Virtualization Library (libOVD):.Start the WLST console.
To do so, run oraclecommon/common/bin/wlst.sh.In the WLST console, run the following command: connectWhen prompted, provide the WLST username, password, and t3 URL.Run the following command to display a list of Identity Virtualization Library (libOVD) WLST commands: help('OracleLibOVDConfig')This lists the commands for creating, deleting, and modifying Identity Virtualization Library (libOVD), LDAP, and join adapters. The following commands act on the Identity Virtualization Library (libOVD) configuration assosicated with a particular OPSS context, which is passed in as a parameter:.addJoinRule: Adds a join rule to an existing Join adapter for the Identity Virtualization Library (libOVD) associated with the given OPSS context.addLDAPHost: Adds a new remote host to an existing LDAP adapter. Note:This procedure does not enable the following functionality:.Forced password changes, including first login, administrator password reset, and expired passwords.Forced setting of challenge responses.Add a dynamic group in Oracle Internet Directory (OID).Create an oimusers.ldif file that defines a dynamic group. The format of the LDIF file should be similar to the following: dn: cn=oimusers, objectclass: orclDynamicGroupobjectclass: groupOfUniqueNameslabeleduri:ldap:// LDAPHOST: LDAPPORT/??sub?(objectclass=inetOrgPerson)For example: dn: cn=oimusers,cn=Groups,dc=us,dc=oracle,dc=comobjectclass: orclDynamicGroupobjectclass: groupOfUniqueNameslabeleduri: ldap:// LDAPHOST:3060/cn=Users,dc=us,dc=oracle,dc=com??sub?(objectclass=inetOrgPerson).Use the ldapadd command to upload the oimusers.ldif file to OID. The command should have the following format: ldapadd -h LDAPHOST -p LDAPPORT -D -w -f oimusers.ldifFor example: ldapadd -h LDAPHOST -p 3060 -D cn=orcladmin -w welcome1 -f oimusers.ldif.Use the ldapsearch command to validate group members.
The command should have the following format: ldapsearch -h LDAPHOST -p LDAPPORT -D -w -b 'cn=oimusers,' -s base 'objectclass=.' For example: ldapsearch -h LDAPHOST -p 3060 -Dcn=orcladmin -wwelcome1 -b 'cn=oimusers,cn=Groups,dc=us,dc=oracle,dc=com' -s base 'objectclass=.' .Configure the LDAP Authenticator in WLS.Log in to WebLogic Administrative Console.Go to Security Realms, myrealm, Providers.Click New. Give a name and choose OracleInternetDirectoryAuthenticator as type.Set the Control Flag to SUFFICIENT.Click the Provider Specific settings and configure the OID connection details.In Dynamic groups section, enter the following values:Dynamic Group Name Attribute: cnDynamic Group Object Class: orcldynamicgroupDynamic Member URL Attribute: labeleduriUser Dynamic Group DN Attribute: GroupOfUniqueNames.Click the Providers tab and then click Reorder. Reorder the LDAP authenticator so this is placed before the OIM Authenticator.Restart all servers.Validate role memberships.Login to WebLogic Admin Console.Go to Security Realms, myrealm, User and Groups.Click users to display all the users in the LDAP user search base.
If the LDAP users are not displayed, it means that there is an error with the LDAP connection, and the details are specified in OID Authenticator (provider specific settings).Click on any user and then to the corresponding group entry. 'Oimusers' should be one of the listed entries. If this validation fails, please go through the LDAP authenticator's provider-specific details.
There's quite a difference between 10.1.4.1 (and earlier versions) and 10.1.4.3 in the syncing business. You may now use multiple profiles quite easily and even have separate jobs for each profile.
Frank@frank-cs03:$ ssh oracle@192.168.1.222oracle@192.168.1.222's password:Last login: Fr Sep 10 16:oracle@oracleas $. OraenvORACLESID = oracle? Iasdboracle@oracleas $ lsnrctl startLSNRCTL for Linux: Version 10.1.0.5.0 - Production on 29-DEC-2010 09:46:40Copyright (c) 1991, 2004, Oracle. oracle@oracleas $ sqlplus / as sysdbaSQL.Plus: Release 10.1.0.5.0 - Production on Wed Dec 29 09:Copyright (c) 1982, 2005, Oracle. All rights reserved.Connected to an idle instance.SQL startupORACLE instance started.Total System Global Area 281018368 bytesFixed Size 779000 bytesVariable Size 229645576 bytesDatabase Buffers 50331648 bytesRedo Buffers 262144 bytesDatabase mounted.Database opened.SQL exitDisconnected from Oracle Database 10g Enterprise Edition Release 10.1.0.5.0 - ProductionWith the Partitioning, OLAP and Data Mining optionsAfter all that, it is time to get ldap running. It needs to connect to the database, so this is the correct starting order. oracle@oracleas $ $ORACLEHOME/ldap/bin/ldapcheckChecking Oracle Internet Directory Processes.ALLProcess oidmon is Alive as PID 2731Process oidldapd is Alive as PID 2749Process oidldapd is Alive as PID 2783Not Running - Process oidrepldProcess odisrv is Alive as PID 2770oidmon (PID 2731) is the OID Monitoring process itself; it is the process, that is actually monitored by opmn.
The two oidldapd processes are two LDAP Daemons. Other than that, there's an inactive Replication process, oidrepld, that is only used in Enterprise-class setups, as IThe final process is the one, I'm interested in: it's the Oracle Directory Integration service, odisrv for short.What if I have no ldapcheck?Well, I did not, either. You can download, unzip it, and rename 'ldapcheckforHPUX' to ldapcheck, do a chmod 740, and you're in business.What id ldapcheck returns. Ps: illegal option - oApply same medicin as 'What if I do not have ldapcheck'Synchronize!Now, in order to get OID to synchronize from AD, I need a few things:. a highly privileged account on Active Directory.
Names, or IP-addresses, of servers involved. an understanding of mapping, with base of OID as well as ADAs for the account, I'll use my own account, which is member of the administrators group - do not use this in production!
But you do need an account, that is allowed to query the 'Deleted users' section - and that requires quite some privileges. If you cannot see 'Deleted Users', users can be removed from AD, but will always remain in OID.
Active Directory Oid 11g Synchronization Login
And that is a security issue.IP addresses: The oracle iAS runs is called oracleas.home.local at 192.168.1.222, the PDC is located at 192.168.1.233.Mapping: well, whoever invented that should be prosecuted. As long as you keep it basic, and simple, there are few problems. As soon as you company is operating multiple domains, it is a RPITA to get things running smoothly. ProfilesMapping is based on profiles. The fastest way to get things running is to take a copy of $ORACLEHOME/ldap/odi/conf/activechg.map.master and use that as basis.The base in OID is dc=bortel,dc=home, as you can see from this picture of the OID Aministration tool, oidadmin:This is the correct entry, as this entry holds the users. Same is true for Active Directory, although I know no other way than to query the darn thing. Cn=users,dc=home,dc=local:cn=users,dc=bortel,dc=homeIn words: maps everything, found under cn=users,dc=home,dc=local (in Active Directory, as it is left of the colon) to cn=users,dc=bortel,dc=home (in Oracle Internet Directory, as it is right of the colon).These are the domain rules.If you have more domains, just add mapping rules.
If you have organized your domain in Units (Organizational Units, or 'ou' in LDAP-speak), start mapping rules at that level, and add, or omit to your needs. DipadminNow, a new tool needs to be used, the dispassistant. User is dipadmin - password of dipadmin is identical to the password of orcladmin:New in this version is the use of Connector Profiles, and profile Sets.Due to badly documented features, and some documentation bugs it is best to create a new Connector Group.First of all, rename the Connector Groups 'configset1' to 'standardgroup'. The original name will just create misunderstanding, as the are configsets in use with OID.Then, create the group you will be using for your actions - the 'standardgroup' will remain as the group holding all defaults, but will not actually be used.
My new group is called 'demo':Next, go to the standardgroup, and disassociate ActiveChgImp:Then, select the newly created group 'demo', and associate the profile:Note, the profile is still Disabled. Edit the profile, and fill in the connection defaults on the first tab:On the third tab, make sure the filter properties do not have quotes around them - it's a bug:On the last tab, I always change 'Continue on Error' to Yes; I have no tools to monitor whether every change gets into OID correctly. Most of the errors I see, are on duplicated entries anyway.You may also want to change the frequency of synchronization: every 60 seconds seems on the high side, escpecially if you have 7 profiles, like my customer, one of which connects to a Active Directory with 13,000 users.Modify the profile mapping file to your liking, and load it into the profile. oracle@oracleas $ dipassistant mp -D cn=orcladmin -profile=activechgimp odip.profile.mapfile=demouser.mapPassword:Profile successfully modified.oracle@oracleas $Results of this process may be found in $ORACLEHOME/ldap/odi/log/bootstrap.log and.trcYou can also inspect the OID with the oidadmin tool:(and see there's a problem with krbPrincipalName.)ActivateNow, all that's left is to start the process of syncs every x seconds.
In order to do that, I'll need to start the connectorgroup. Said.Hi,We have one system says hr system which take care of entering all the user information. Once it submit that information it goes to oid. Now we want that when we import all that user from oid to active directory it didn't duplicate any user as well as depending on their role it should create groups dynamically in active directory. For e.g: If user belong to Trainee category or manager category it must create Trainee group & Manager group & respective person should go into that group.
Active Directory Oid 11g Synchronization Log In Firefox
I don't know whether my question is placed in right group or not. Any help will be appreciated.Thanks,Sonya Sharma.